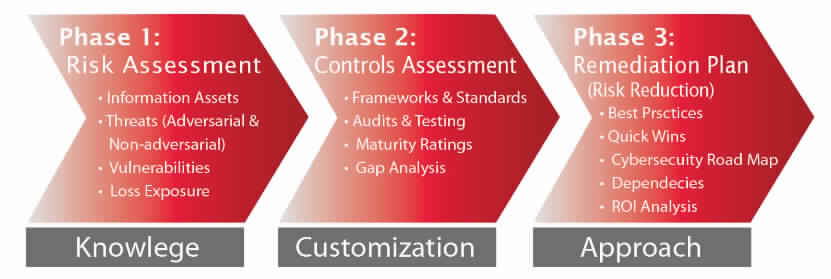
The purpose of the risk assessment is to evaluate the adequacy of organization’s security. The risk assessment provides a structured qualitative assessment of the operational environment.
It addresses sensitivity, vulnerabilities, risks and safeguards. The assessment recommends safeguards to mitigate threats and associated exploitable vulnerabilities.
Approach to provide the service
This risk assessment methodology and approach is conducted using the Defense In Depth methodology. The assessment evaluates security vulnerabilities affecting confidentiality, integrity, and availability. The assessment recommends appropriate security safeguards, allowing management to make knowledge-based decisions about security-related initiatives Risk Assessment Process.
This section details the risk assessment process performed during this effort. The process is divided into two sections: pre-assessment and assessment.
Phase I : Pre-Assessment
Step 1: Identify business processes and define the assets
Step 2: Data Collection
Phase II : Assessment
Step 1: Document Review
Step 2: System Characterization
Step 3: Vulnerability Identification
Step 4: Risk Determination (Calculation/Valuation)