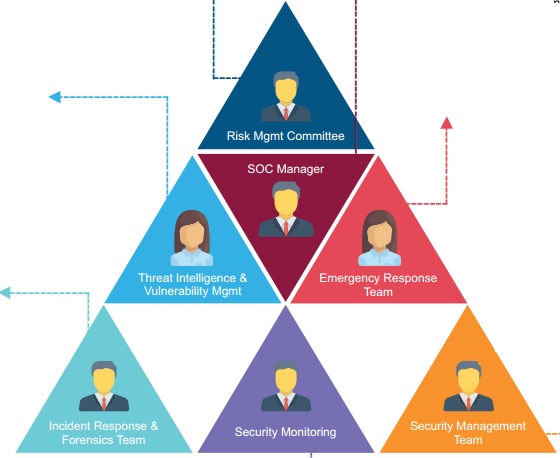
SOC Manager
– ITIL Certified
– Manages resources to include personnel, budget, shift scheduling and technology strategy to meet SLAs;
– Communicates with management
– Serves as organizational point person for business- critical incidents
– Provides overall direction for the SOC and input to the overall security strategy
Risk Management Committee
– Impact and Risk Assessment of Incidents
– Manages Risk, Compliance and Governance
– Alignment of Risk Management with Business Needs
– Qualified Risk Ranking
Threat Intelligence & Vulnerability Mgmt
– Network Scanning
– Vulnerability Scanning
– Situational Awareness
– Security Consulting
– Ethical Hacking
– Gap Analysis
–
Develop intelligence from their past incidents and from
information-sharing sources, such as a specialized threat intelligence
vendor, industry
partners, the cybercrimes division of law inforcement information sharing organization
Emergency Response Team
– Subject matter Experts
– have vast knowledge and experience with network threats, their detection and mitigation, and in-depth experience.
– Provides expert security assistance
– Take immediate corrective action to restore services and attack mitigation
– Handling Major (High Priority) Incidents andVulnerability Mgmt escalations
Incident Response & Forensics Team
– Expert of security technology and process
– Understand attacks and threat matrix
– Extremely good at reaching to rootcause
– Think out of box
– Understand Virus, Trojans, backdoor, malicious code
– Performs deep-dive incident analysis by correlating data from various sources
– Determines if a critical system ordata set has been impacted
– Advises on remediation
– Provides support for new analytic methods for detecting threats
Security Monitoring
– Continuously monitors the alert queue
– Triages security alerts
– Monitors health of security sensors and Network Elements
– Collects data and context necessary to initiate Investigate and Analysis work.
Security Management Team
– Expert of Security, OS, Network, Web technology, Database
– Configure tools and security technologies
– Implement security policies in technologies under SOC
– Quick at Incident response
– Interact and drive vendors, OEM,Government bodies
– Handles Day to day operations of the
– Device Administrations
– Configuration Management as per the change request policies
– Device Configuration Backups